The Internet of Things is one of the most popular technologies in today’s technological revolution but still faces many IoT challenges. As devices and technologies become connected and smarter, so do the dangers and vulnerabilities they face. In the past decade, the Internet of Things has been widely used in various industries, with many companies using it to develop smarter operations.
While IoT devices bring about efficient communication between devices, automation, time and cost savings, and many other benefits, there is also one thing about users, and that is not security. IoT devices are hard to trust on certain occasions. This article will tease out some of the key IoT challenges in each link.
1. 8 IoT Challenges in Security Issues

Non-consistent safety standards
The Internet of Things is somewhat outdated in terms of security standards. There is no uniform standard for niche markets and businesses, which means that all businesses are required to set up their own guidelines and protocols.
The lack of standardization makes it tougher to secure Internet of things devices and to communicate between M2M without increasing the risk.
Low processing capacity
There are very little data is required for most IoT applications. This lengthens battery life and reduces costs, but makes OTA updates more difficult and prohibits devices from using network security tools. Therefore, hacking tends to happen.
Legacy assets
Developing applications without cloud connectivity is vulnerable to modern cyber-attacks. For example, these older assets may not comply with the new encryption standards. It’s dangerous to let old applications run on the Internet without making big changes, but that’s not always possible with historic assets. These technologies have been pieced together — possibly for decades — and even small security updates are a major IoT challenge.
Lack of awareness
Internet users have learned how to protect mobile phones and personal computers over the years. But because the Internet of Things is a new technology, many people are unfamiliar with its concepts and functions. Hence, consumers, businesses and manufacturers are able to pose security threats to Internet of things devices. Hackers attack people and equipment.
Botnet attacks
Botnets are networks of linked devices that hide malware, enabling hijackers to commit all sorts of fraud. Such bots are adopted to carry out server crashes, unauthorized access, distributed denial of service, and data theft.
The usual goal is to develop, automate, and accelerate attacks in a short period of time and consumes less expense. To attack effectively, a hacker can remotely access a device and infect thousands of workstations. It is difficult for a secure system to distinguish real communications from malicious ones.
Lack of encryption
In the Internet of Things, the lack of traditional transmission encryption is one of the biggest security problems. They are able to obtain sensitive information sent to and from the device once someone breaks into the network.
The firmware update is missing
Another big issue for IoT security is whether the deployed devices are vulnerable. Manufacturers are supposed to upgrade their firmware whether it comes from their own code or code generated by a third party. In theory, this should be possible remotely, but this is not always possible. When data is moving too slowly across the network or message capacity is limited, you may need to physically contact the device to release updates.
Prohibited and counterfeit Internet of Things devices
Closing borders and managing all individual devices are major challenges in IoT security. The popularity of Internet devices and the rapid increase in the number of manufactured devices have caused problems with home networks.
Unauthorized users install illegal and fake IoT devices on protected networks.
Such devices are allowed to be configured as malicious access points, thermostats, and cameras to steal communications data without the user’s knowledge.
2. Internet of Things(IoT) challenges in Data Privacy

Privacy is a major concern for businesses. The issue of how to better protect sensitive and personal data has become increasingly prominent in recent years, as legal and regulatory frameworks such as the GDPR have received increasing attention and the cyber threat landscape has become more dynamic and complex.
IoT is transforming multiple industries, and the automation and business intelligence it facilitates are powerful. But the IoT also presents specific challenges for organizations in terms of data privacy. Let’s learn from the content below.
The endpoint increase
IoT sensors or devices are connected to the Web. This, in turn, means that IoT devices or sensors are potential points of data leakage, or that malicious parties can gain access.
Thus, when an organization creates an IoT ecosystem, for example, by deploying networked sensors across the entire physical assets of a factory floor, each of those physical assets is theoretically an end device, just like computers and mobile devices elsewhere in the organization. As a result, the group has greatly increased the attack surface, in which cybercriminals can try to gain access to networks through terminal devices in order to steal data.
Small and simple devices
It’s not just the number of IoT devices that raise privacy concerns, but the simplicity and small size of many of them. This usually means that it is impossible to embed advanced network security protection in these devices, resulting in malware infection and malicious data interception. Other problems may include setting easy-to-remember passwords to default passwords.
Data increase
IoT devices collect data that was impossible to collect or expensive. This data generates vast amounts of business intelligence that can be harnessed in real-time and over the long term. In short, they dramatically increase the number of data organizations is handling — which, in turn, means that security and privacy experts should be concerned about how that data is collected, processed, shared, and stored.
To implement a robust approach to data privacy protection, organizations that process data, especially personal data, need to map that data flow across their business and draft and enact security policies related to that data.
Visibility is key
These data privacy and protection issues are possibly to be multifaceted, but they are not insurmountable. Instead, companies engaged in developing or deploying IoT devices need to make data protection a priority from the outset, not an add-on for later consideration. Strong data privacy always starts with visibility — understanding what data is being collected or generated, where and how it is being processed, and how it is being stored.
3. IoT Challenges in Wireless Communication Connectivity
While the full scope of the Internet of Things is still being debated, it’s obvious that these devices are at a crossroads as they transition from “good to have” to “essential,” and people will increasingly rely on these devices to perform mission-critical and, sometimes, critically important applications.
Wireless communication is crucial for Internet of Things devices. ZigBee, Z-Wave, Bluetooth, NB-IoT, and Wi-Fi are preferable options for designers to enable this communication. Internet of thing devices must operate across multiple users with different wireless technologies and the same spectrum in mission-critical scenarios.
In large buildings (such as hospitals), intensive equipment operations must be provided and reliable wireless communications must be carried out. Patient tracking devices, smart lighting, wearable devices, medical devices, and security systems carried by visitors must operate simultaneously and not interfere with each other. This situation exists in hospitals, where medical surveillance equipment shares the 2.4 GHz ISM band with mobile phones, wireless cameras, and microwave ovens. It is critical to ensure that the operation of an IoT device works as intended in this type of environment.
Network challenge
With the advent of 5G, more and more applications will utilize improved cellular network performance to “stream” computing workload to data centers. Devices of all kinds can be supposed to be connected to the network, some of which may intentionally pose a threat to network security and integrity. Therefore, systems and network management tools must be developed to mitigate such risks.
IoT capabilities are now being designed for use in increasingly critical applications across all industrial sectors. Designers must follow a well-thought-out process to design, test, and validate their smart devices and systems. The process must involve measurement and testing at the wireless communications, network levels, and devices.
Luckily, designers now have a variety of testing choices available to help verify the functionality of the IoT ecosystem. But doing the right tests is not enough. Designers must adopt the right tools to do the right job.
Battery consumption analysis helps designers accurately determine the current usage of the device and the duration of each operating mode. Accurate modeling tools and EMI simulation can help estimate emission levels prior to hardware development.
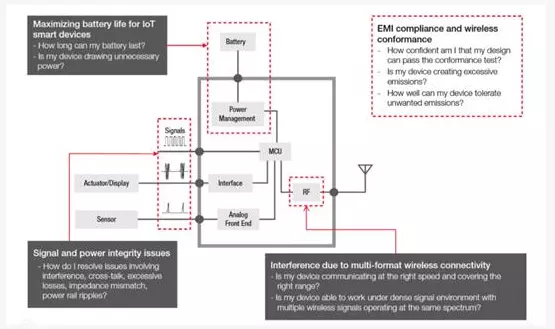
4. Common IoT Development Challenges
Sensor module
Sensor modules are typically designed around microcontroller units that have digital and analog interfaces, and RF transceiver interfaces are also required to communicate with the outside world.
Block diagram of an IoT sensor module
Power management and sizing are common challenges for designers. RF interfaces can consume a lot of power. Low-power wireless protocols have been developed to offer a trade-off between power consumption and transmission range. Power consumption and smart factories in some environments may not be an issue compared to the requirement that multiple devices must communicate without interference. Signal integrity becomes an essential priority. In addition, electromagnetic interference requirements must be complied with in industrial environments.
Designing IoT devices with optimal battery life requires accurate power consumption curves and accurate characterization of the dynamic load on the device. Understanding the relationship between load requirements, and time required is an essential aspect of determining possible battery life.
Whether it is a non-rechargeable button battery or a rechargeable LiPo battery, the operating characteristics of the battery need to be understood and incorporated into a complex power management program to extend and optimize battery life. Being able to accurately track battery loads and how requirements can help.
Designers can develop powerful power management processes by using this information. The designer may determine, for example, that the current of the IoT device has a very wide dynamic range during operation, from hundreds of milliamps when the wireless transceiver starts the link to submicroamps when the transceiver is off, up to the microcontroller is at maximum. Optimal sleep patterns, sensors are not activated, and so on.
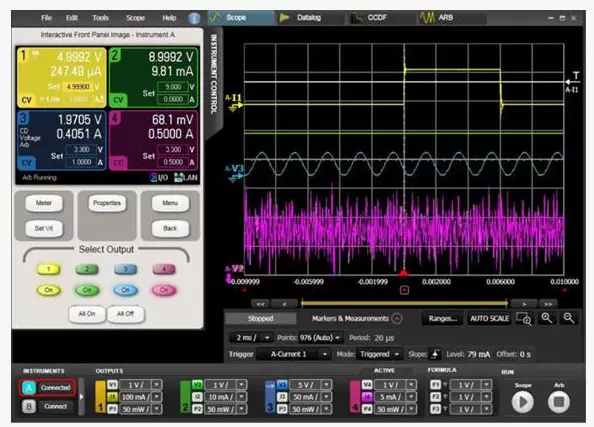
Figure 2. It is critical to optimize battery life to analyze battery consumption in wireless IoT devices. The N6705B DC power analyzer and N6781A two quadrant source measurement unit are ideal tools for characterizing battery consumption and understanding equipment changes over time with battery load.
Long battery life
Many IoT device users today require that they have batteries that last for years. This is especially important if someone is planning to deploy something in a remote area where they can’t easily access change batteries. Operations or otherwise putting someone at higher risk of complications may be needed by frequent battery changes.
Hardware designers should think about which aspects will consume the most power and whether it’s necessary to include them in the design.
Using integrated circuits that have deep sleep patterns and consume very little current can solve this challenge. Moreover, designers should also take consideration into how to use low battery voltages. For example, minimize the current consumption of the product. Designers can achieve this by using low-power components and ensuring that parts do not continue to consume too much power when not in use.
Researchers who have commented on the project believe significant progress will be made by developing batteries that can charge themselves.
Security vulnerabilities
Current headlines often contain alarming details about security vulnerabilities that could affect IoT devices around the world. A multi-pronged approach is required to solve this internet of things design challenge from a hardware perspective.
First of all, designers must consider secure key management. Using hardware-accelerated encryption to keep devices more secure is also an option.
Separate memory domains are also a preferred method. Use secure memory access to protect flash memory and RAM from unauthorized access. Doing so makes it harder for hackers to launch attacks using programming interfaces and debuggers.
Push for lighter, smaller devices
The desire for these features is justified as it enables flexibility in implementation.
One possibility is to see if the device needs to use flexible printed circuit boards (PCBs) instead of rigid ones. More components are allowed to be packed into a smaller space. They are also generally more durable than rigid ones and can withstand shocks in harsh environments better, giving them a longer overall life span.
If IoT devices will be used in conjunction with artificial intelligence (AI) or processing data on the devices, hardware designers must understand that these necessities also affect form factor dimensions.
IoT hardware designers should keep up with these developments and understand how newer options support their upcoming products.
Invest enough time in testing
Designers usually operate on a tight schedule. Even so, they must allow enough time to test the hardware and make the necessary adjustments once the results are in.
Testing before a product is marketed can also prevent safety-related problems. For example, fuzzy testing involves getting IoT devices to accept random bytes and track abnormal behavior that might indicate an error. This most often happens when testing a computer application. But, it’s also a good method to check the internet of things devices.
Effective communication across teams is critical to obtaining useful test results. Software developers working on the device may find errors that partially affect the hardware.
Establishing a stable relationship with testers is also important. Many of these parties may not immediately know that they are experiencing problems due to hardware issues. However, after detailed feedback from those involved in testing, hardware designers and others involved in IoT products can begin to figure out where the problem is and collaborate to fix it.
Hardware designers should always plan to spend more time testing than expected. This way, there is no pressure to rush things, and there is no chance of missing issues that could interfere with product functionality or safety later on.
Foresight prevents many IoT design challenges
There is no one-size-fits-all way to avoid every IoT design challenge. But it is critical to consider the good and bad consequences of each design decision. Designers can also be able to make the most suitable options at each stage and avoid time-consuming problems.
5. IoT Challenges in Deployment

IoT deployment has expanded from consumer-based applications like smart home devices and wearables to mission-critical applications in industrial automation, emergency response, public safety, IoMT, and autonomous vehicles.
The “5C” for the IoT are the 5 primary challenges facing IoT design, namely continuity, connectivity, compliance, network security, and co-existence.
Deployment challenge 1: Connectivity
Achieving a seamless flow of information to and from devices, infrastructure, cloud, and applications is one of the larger IoT challenges because of the complexity of intensive device deployments and the complexity of wireless connectivity. However, mission-critical IoT devices are expected to function reliably without failure even in the harshest environments.
Solutions are required to be designed and tested that are highly configurable, flexible, and scalable to meet future requirements to address connectivity challenges. Flexibility needs to test devices with multiple radio formats in actual operating mode and to support OTA testing in signaling mode without chipset-specific drivers. To leverage the code and minimize measure-related issues at different stages of development, the solution should be inexpensive, simple, and able to be used in manufacturing and R&D.
Deployment challenge 2: Continuity
Ensuring and extending battery life is essential. Longer battery life is a big benefit. For IIoT devices, battery life is typically 5~10 years. Device life means the difference between death and life for medical devices. However, battery defect is also a problem.
IC designers are required to design ics with deep sleep modes and reduce instruction and speed sets and achieve low battery voltages to meet the IoT battery life requirements, integrated circuit.
Standards bodies are defining new low-power operating modes like Sigfox, LTE-M, LoRa, and NB-IoT, which maintain low power consumption while providing limited effective operating time.
Deployment challenge 3: Compliance
Internet of things devices are necessary to comply with global regulatory requirements and radio standards. Conformance testing includes radio standard conformance and carrier acceptance testing, as well as regulatory compliance testing, such as RF, EMC, and SAR testing. Design engineers are usually forced to adhere to strict product launch schedules in compliance with the latest regulations
As compliance testing is time-consuming and complex, days or weeks are required to complete if performed manually. In order to keep the release schedule, designers can consider investing in in-house pre-conformance testing solutions that can be used at every design stage, as well as resolving problems early. Selecting a system that meets the regulatory compliance requirements of the test lab can also help ensure measurement relevance and reduce the risk of failure.
Deployment challenge 4: Coexistence
For billions of devices, congestion in radio channels is a problem that is only going to get worse. Standards bodies have developed tests to assess how devices operate in the presence of other signals to solve wireless congestion.
For example, in Bluetooth, adaptive frequency hopping (AFH) enables Bluetooth devices to abandon channels that encounter high data collisions. Other collision avoidance technologies, such as LBT and CCA, can also improve transmission efficiency. But the effectiveness in mixed-signal environments is unclear, and when radio formats cannot detect each other, conflicts and data loss can occur.
An industrial sensor that loses control of its signal can have serious consequences. Coexistence testing is therefore essential to measure and evaluate the operation in crowded mixed-signal environments and to assess the potential risks of maintaining wireless performance when unexpected signals are found in the same operating environment.
Deployment challenge 5: Network security
Most traditional network security tools are focused on the web and the cloud. OTA and Endpoint vulnerabilities are often overlooked. Little work has been done to address OTA vulnerabilities through mature technologies such as WLAN and Bluetooth used in many applications.
70% of security vulnerabilities come from endpoints. To protect these IoT devices, extra care should be taken. Potential entry and OTA vulnerabilities points into endpoint devices should be identified, and devices should be tested with a regularly updated database of known threats/attacks.
Build a solid Internet of things foundation through “5C”
It opens the door to exciting new opportunities and applications for many industries. But it also presents unprecedented challenges, requiring new ways of thinking to meet mission-critical requirements. Delivering a successful IoT means overcoming the 5C technology IoT challenge. The IoT delivers on its promise and will be ensured by using the right validation, compliance testing, manufacturing, and security tools throughout the product life cycle.
6. Supply chain challenges of the IoT industry

Basic overview of consumer Internet of Things
IoT refers to connecting any object to a potential network as per a specific transmission protocol and realizing the intelligent connections between things, things, people, and people through real-time transmission and collection of multi-dimensional information. As a representative of the third revolution in the information technology industry, the IoT organically combines AI computing AND traditional industrial manufacturing. The IoT is primarily divided into Industrial Internet of Things and consumer IoT.
The complete IoT is mainly composed of the network layer, application layer, perception layer, and platform layer. As the integrator of the Internet of Things, the application layer undertakes the important responsibility of realizing product functions for end-users. The company’s main product, intelligent audiovisual hardware, belongs to the application layer of the consumer Internet of Things. Consumer IoT, smart office, smart travel, and smart home are In the application scenarios of consumer IoT.
Data is the core resource of the IoT era
Intelligent terminal is the entrance to the Internet of Things to obtain data: The evolution path from the Internet era to the Internet of Things era is generally summarized as follows: Internet (PC, 1.0 era) → mobile Internet (smart phone, 2.0 era) → Internet of Things (intelligent terminal of human-computer interaction and Internet of everything, 3.0 era), and each upgrade is centered on the mining and redistribution of traffic data, the core resource. The Internet of Things will break through the existing “people” connection, expand to “people”, “people and things”, “things and things” “Internet of everything”, and on this basis to generate more large-scale data, more powerful AI. The core resource of the Internet of Things era is data. Whether it is chip, sensor, intelligent terminal and other hardware manufacturers, or communication operators, cloud platforms, artificial intelligence and other software service enterprises, those who can obtain more data information will have a greater say in the whole industrial chain. The premise of acquiring big data of the IoT is to set up an intelligent terminal network with large flow data collection capability.
The scale of the Internet of Things industry continues to grow
Consumer Internet of Things has broad market prospects: The White Paper on Terminal Security of the Internet of Things (2019) shows that in recent years, applications of the IoT have emerged endlessly, and the popularization and application of smart medical, intelligent transportation and other industries have comprehensively promoted the exponential growth of the Internet of things terminals. The number of connected devices the IoT in the world reached 11 billion in 2019 and will reach 25 billion by 2025. Compared with 2018, it achieved a compound annual growth rate of 15.71%.
In the field of consumer IoT, the number of global consumer Internet of Things connections is expected to grow to 11.4 billion by 2025, among which the number of smart home devices represented by home security devices is supposed to increase by 2 billion.
In terms of industry size, global revenues such as IoT products and services were $343 billion in 2019 and are expected to grow to $1.12 trillion in 2025, with an annual growth rate of 21.86%.
Advances in communication technology, cloud computing, and AI support the rapid development of the Internet of Things industry
As the link of the Internet of everything, the development of the IoT cannot be separated from the progress of network and communication technology. Due to the limitation of transmission and computing capacity, traditional 4G networks and centralized computing cannot handle the massive data brought by the Internet of Things and cannot realize the idea of real-time interconnection. As new technologies such as 5G, cloud computing, and artificial intelligence mature and converge, the foundation for the development of the Internet of Things industry has been laid.
5G communication is the latest generation of cellular mobile communication technology. Compared with 4G, 5G network has the advantages of a higher transmission rate, lower time delay, and more connections, which can meet the higher requirements of network transmission and connection for cloud offices, smart cities and industrial automation. In its 2019 global Exhibition Industry Outlook (GIV@2025), Huawei predicted that by 2025, 58 percent of the world’s population will have ACCESS to 5G networks, 14 percent of households will have “robot butlers,” and 97 percent of large companies will adopt AI (artificial intelligence).
Cloud computing refers to the process in which computing programs with a large amount of data are divided into numerous smaller programs, which are processed and analyzed by a system, and the calculation results are returned to users. Cloud computing, as a distributed computing, integrates more server resources and has powerful data processing capabilities by improving reliability and scalability, providing solutions for massive data processing in the Internet of Things era. Experts forecast the global cloud market to be around $273.3 billion in 2022, up 212% from 2016. AI is a science that specializes in the study of human intelligence, and makes machines possess the characteristics of human intelligence through simulation, extension and extension. The core of AI is algorithms. Through the improvement of algorithms and computing power, artificial intelligence products have the ability of image processing and language recognition. The global AI market was estimated at us $680 billion in 2020, with an average annual growth rate of 32% from 2015 to 2020.
Development situation and trend of consumer Internet of Things intelligent hardware industry
Intelligent terminal of consumer Internet of Things refers to terminal hardware products with information collection, processing and connection capabilities, and capable of realizing intelligent perception, interaction, big data services and other functions. It is an important carrier of artificial intelligence in the Era of Internet of Things and an important link in the industrial chain of consumer Internet of Things. As emerging industries and an important part in the field of consumer electronics, intelligence of the end products such as mobile phones, TV, a new generation of information technology is accelerating and intelligent household, automotive hardware, wearable devices, mobile medical treatment and so on the Internet of things intelligent terminal product integration, suggesting the intelligent hardware industry to flourish, drive mode innovation and efficiency.
Smart hardware is exploding
Since 2016, China has successively issued a number of laws, regulations and policy documents, including “Special Action for Innovation and Development of Intelligent Hardware Industry” and “Guidance on Promoting and Regulating the Application and Development of Health and Medical Big Data”.
In terms of demand, with the growing level of national economy, the consumption structure of residents continues to upgrade, and the service fields such as entertainment, medical care and education usher in continuous changes. High-end, intelligent and customized products represented by intelligent hardware continue to lead the development of the industry. At the same time, as the main consumer group in China is gradually shifting to the post-80s and post-90s generation, the consumption standard is also gradually developing towards diversification and quality. Intelligent hardware products represented by wearable devices, smart speakers, smart doorbells and so on are widely favored by the market.
On the supply side, with the rapid development of China’s 5G, cloud computing, artificial intelligence, Internet of Things and chip industries, China has gradually formed a complete intelligent hardware industry supply chain. With the deepening of enterprise cooperation, the logic of the underlying products in the intelligent hardware industry will continue to be consolidated, and the cooperation in r&d, production and sales will become increasingly close. As China matures in the field of information technology, relevant education in colleges and universities continues to be carried out, and the quantity dividend of Chinese engineers will continue to ferment, driving the rapid development of intelligent hardware-related industries.
Cooperation in the intelligent hardware industry continued to deepen
With the continuous development of intelligent hardware industry, the cooperation between upstream and downstream enterprises of the industrial chain also continues to deepen. In the process of intelligent hardware products, intelligent hardware scheme requires traders and manufacturers from product conception, design, research and development to production and sales of the whole stage, with the telecommunication operation industry chain upstream and downstream enterprises, platform service enterprises work closely and algorithm processing enterprises and other enterprises, relying on the advantage of each enterprise and field continues to build all-round cooperation, Build a complete product underlying logic, and jointly develop intelligent hardware products to meet user needs.
In the process of deepening cooperation of industrial chain, the cooperation between artificial intelligence algorithms and intelligent hardware is particularly close. Intelligent hardware with optoacoustic data acquisition and processing functions represented by intelligent network cameras, vehicle data recorders and Bluetooth headsets has gradually become a new entrance for human-computer interaction, and artificial intelligence technologies such as image recognition, face recognition and voice recognition have been applied in industry. With the continuous maturity of industrial chain technologies, the development of artificial intelligence, Internet of Things, cloud computing and other technologies has greatly promoted the technological upgrading of products, improved product market performance by optimizing product user experience, and become a new hot spot in the industry.
The range of intelligent hardware applications is rapidly expanding
Increasingly rich application scenarios: With the continuous development of artificial intelligence, intelligent hardware products continue to grow and expand to segmented fields and specific scenes. Products tend to be scenario-oriented, and products and services for market segments continue to emerge. At present, intelligent hardware has been widely applied in smart homes, smart cities and other scenarios.




















